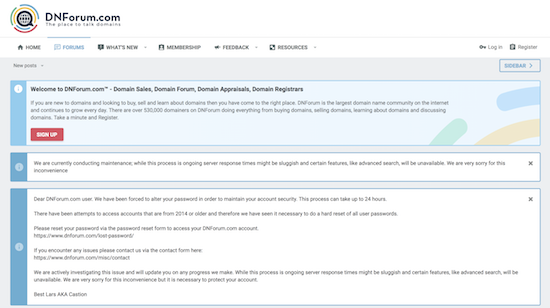
Earlier this morning, I unexpectedly received a password reset request at DNForum. I was previously an active user on DNForum, but I have not used the forum in quite some time. As a result, I was taken aback that a password reset email was sent to me. It looks like I was not alone in receiving the reset notification, as others have mentioned receiving the same password reset email.
When I visited DNForum this morning, I saw a message on the home page alerting visitors to the automated password reset request that was sent to users. Here are the two notes currently on the homepage of DNF:
“We are currently conducting maintenance; while this process is ongoing server response times might be sluggish and certain features, like advanced search, will be unavailable. We are very sorry for this inconvenience”
Here’s the note referencing the password reset:
“Dear DNForum.com user. We have been forced to alter your password in order to maintain your account security. This process can take up to 24 hours.
There have been attempts to access accounts that are from 2014 or older and therefore we have seen it necessary to do a hard reset of all user passwords.
Please reset your password via the password reset form to access your DNForum.com account.
https://www.dnforum.com/lost-password/If you encounter any issues please contact us via the contact form here:
https://www.dnforum.com/misc/contactWe are actively investigating this issue and will update you on any progress we make. While this process is ongoing server response times might be sluggish and certain features, like advanced search, will be unavailable. We are very sorry for this inconvenience but it is necessary to protect your account.
Best Lars AKA Castion”
It is always a good idea to ensure your passwords are not repeated on multiple websites. If they are repeated, if one site gets hacked someone could gain access to other websites that use the same username / email and password combination.
If I learn anything more about this, I will provide an update.


It might be too late Elliot.
About a month ago I started receiving threats from a Third Party to make payments to remove malware they had allegedly inserted. They used my DNForum user name in the content even though I have not been active on theta forum for many years.
I believe there has abeen a security breach and data stolen. I need to see a fully detailed explanation from them as a matter of urgency.
Remove malware from where?
Sorry – I am not totally following what transpired.
The Third Party emails state that they have “inserted malware software into my computer system” unless I make a payment to them. I have emailed DNForum for an urgent explanation as to what happened and why notification has been so irresponsibly delayed.
>> receiving threats from a Third Party to make payments to remove malware they had allegedly inserted
It’s just a scam email sent out but criminal gangs who are using scripts to mailbomb using leaked datasets
1. check you’ve not reused the same password multple places (if so update them ALL immediately)
2. bin the threatening email
I thought DNF had died a long time ago, but it does from the emails, note on their site and other reports sound like their DB has been leaked at some point or at the very least “scraped” forums are regular targets due to the (short term) SEO benefits that miscreants can monetise from abusing the posts/sigs/etc
I get emails from people who wants me to pay via bitcoin , if not they will expose my sex videos to all my contacts. Sabotage and ransom.
That the big reason why bitcoin should be abolished. You can’t trace!!
That’s unrelated. Those are bulk scam campaigns. They have no idea who you are and have nothing on your computer. You can safely ignore them; just mark them as spam. It’s the same as any other scam email.
Those are standard scam emails. They predate bitcoin. The methods they used prior to that were equally untraceable. They don’t have your contacts and they don’t have videos of you; they have no idea who you are. They’re just trawling for anyone gullible enough to believe the messages. Mark them as spam and ignore them.