Late last year, I discovered and shared that people are able to contact domain registrants directly via the GoDaddy Whois lookup page. This may be helpful because domain registrant contact information was recently removed from GoDaddy Whois lookup pages. Earlier this week, I discovered a change in the format of the GoDaddy Whois contact form – instead of a custom message field, I was given four contact options from which to choose:
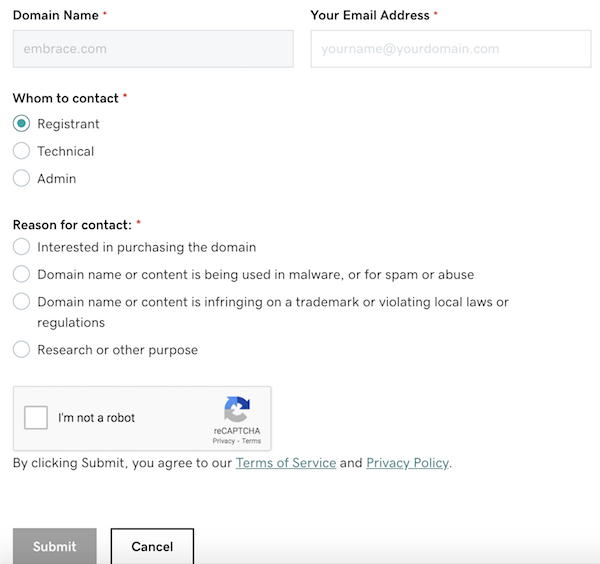
I shared what I found on Twitter:
GoDaddy has changed the format on the Whois contact form. You can now choose from several options, and an automated message is sent to the registrant. You can no longer send a customized message. https://t.co/YtVeDMItcR
— Elliot Silver (@DInvesting) August 13, 2020
George Kirikos replied to my tweet, and he said that he could still see the other form, which would allow for a customized 100 character message to be sent:
Maybe they are A/B testing, or still rolling it out to everyone, as I just tried it on a domain but could still enter up to 100 characters.
— George Kirikos (@GeorgeKirikos) August 13, 2020
I checked again from my Chrome browser, and I still see the drop down menu option, preventing me from sending a customized message to the domain registrant. However, when I used an Incognito mode browser, the old Whois contact form was there, allowing me to customize my message. I tested a few different times, both in standard and Incognito modes, and I noticed different forms for each. This, in my opinion, would indicate that GoDaddy is testing the form.
This contact form, which is apparently an ICANN requirement, is likely a target for scammers and schemers since delivery is seemingly guaranteed and the message comes via an official GoDaddy account email. In fact, attorney Jason Schaeffer reported that clients received scammy “offers” via this channel. GoDaddy could be trying to reduce the volume of spam or scam messages.
When I tested the new version of the form and selected the “Interested in purchasing the domain” option, here’s the email that was sent to the registrant email address:
Someone is trying to contact you regarding [domain name].
We received a request from someone who’d like to contact you regarding [domain name], which you registered through GoDaddy. This contact method is designed to provide a way for people who are interested in your domain to reach you, while still keeping your contact information private.We’re required by ICANN regulations to forward these types of requests to you, and you’re not under any obligation to respond.
Remember, we have no information on the legitimacy of these contacts, and scammers have been known to try to pose as GoDaddy or other companies. Use caution when viewing or replying to unsolicited messages from third parties. If you determine you would like to respond to this message, please be aware that you are electing to respond directly to a third party that has no affiliation with GoDaddy.
Here is the message from info@embrace.com. Once again, this is NOT from a GoDaddy representative.
I am interested in purchasing this domain. Please respond if you are interested in selling.
To respond directly to the requester, simply reply to this email.
I was glad to see that GoDaddy removed the customer account number from the email, which is something I privately suggested when I noticed the form last year. Previously, if the recipient of the email replied directly from the contact email, the sender would see the person’s customer account number. I don’t know how risky that is, but I suppose it is a piece of information that theoretically could have been used for social engineering.
It will be interesting to see if GoDaddy is storing the data collected from this form. I assume they are, so it will be more interesting to see if GoDaddy uses this information for marketing or other purposes.



That’s interesting. Better than the old way. But you should still be able to send a message though.
There are two obvious problems with this contact form.
First – the contact form links to GoDaddy’s general terms and privacy policy, but neither of those two policies state that the user’s email will be send to the domain registrant. The form does forward the email address, but the user is never informed of that fact, and neither of the linked policies mention that fact.
Second – This is the fun one. There is no verification loop on the email. In other words, the form does not cause a verification email to be sent to the entered email address. This provides a great opportunity for mischief. If you know (and can easily find out through a variety of sources) the email address of someone associated with a trademark owner or their attorney, then you can send an “I want to buy this domain name” inquiry through the form to the registrant. The registrant, who might otherwise have registered and been using a name for legitimate purposes, might then send an email to that email address, proposing terms for selling the domain name, in the incorrect belief that they had received a purchase inquiry. In some instances, that apparently-unsolicited sale proposal may be enough to trigger a UDRP or ACPA action by the trademark holder.
Have at it, folks.
1. A “verification loop” isn’t necessarily a good thing if it’s improperly setup, as it can create a mechanism whereby an attacker can send unwanted messages (spam, etc.) to *that* manually-entered email address that is unrelated to WHOIS.
e.g. the WHOIS email of example.com is whois@example.com, but attacker wants to send a message to george@example.NET. Attacker creates a message that is purportedly to the owner of Example.com, whereby they input a “from” email of george@example.net. If a poorly implemented “verification” email is sent to george@example.net, e.g. “please verify that you want to send the following email to whois@example.com“, then an anonymous attacker can get their email message delivered to george@example.net without any identity info at all, which is ripe for abuse.
A better system would be to force a signup by those intending to send messages, and verify that signup. When verified, they’d be able to login, and then send messages to WHOIS contacts. That verification wouldn’t transmit any meaningful message, and should allow explicit unsubscribing, to prevent fraudulent signups (I’m sure many of us have received unwanted signups, and some of those don’t allow any on to explicitly remove themselves easily).
2. Another issue, which affects GoDaddy’s current web-based WHOIS, as well as this contact form, is the use of Google’s reCAPTCHA. Many Google services are blocked in China, which means that those in China who want to contact owners of domain names via WHOIS can’t see that information at all (or can’t use the contact form), because they can’t get past the reCAPTCHA (not everyone in China uses VPNs!). So, I’d suggest using a different CAPTCHA system, or allow folks an alternative, such as a login system to prevent/monitor for abuse. Other registrars suffer from this issue too, not just GoDaddy.
But at least we are safer (insert sarcasm here).
Third – there are tracking pixels embedded in the HTML format email that GoDaddy sends when someone uses the form.
It would be very interesting with the rest that Godaddy has acquired who do a lot of allowed mischief.